-
Security visualization
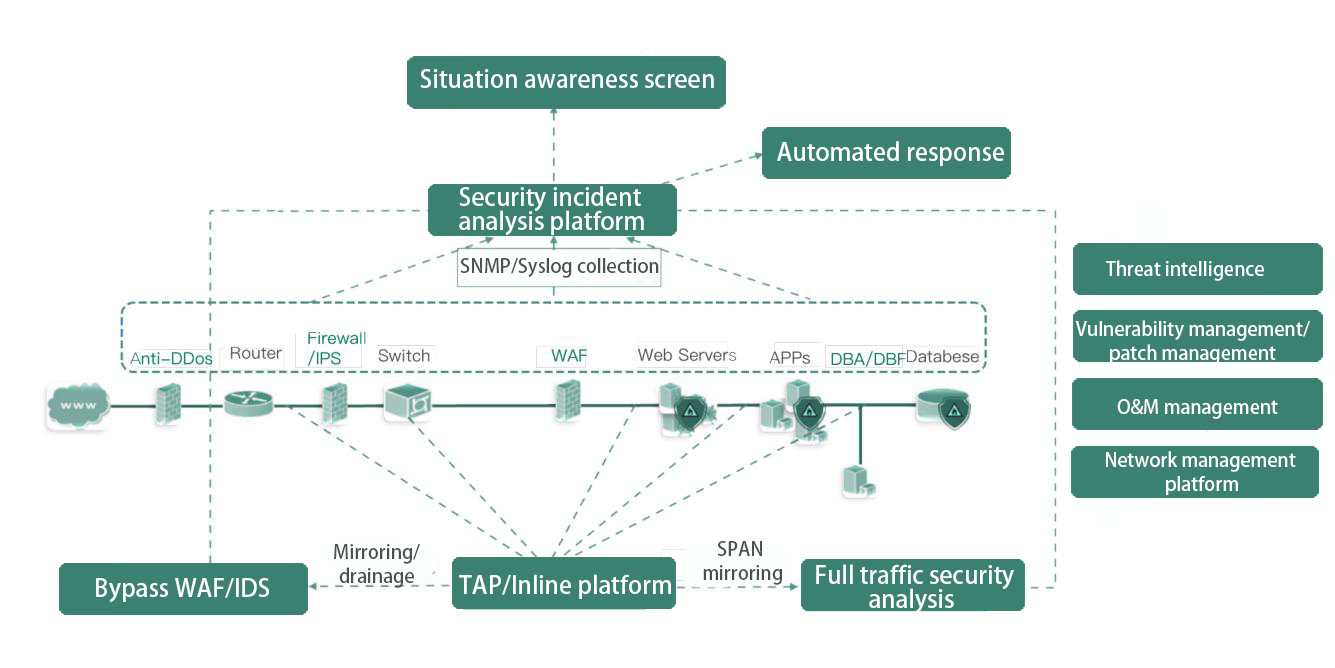
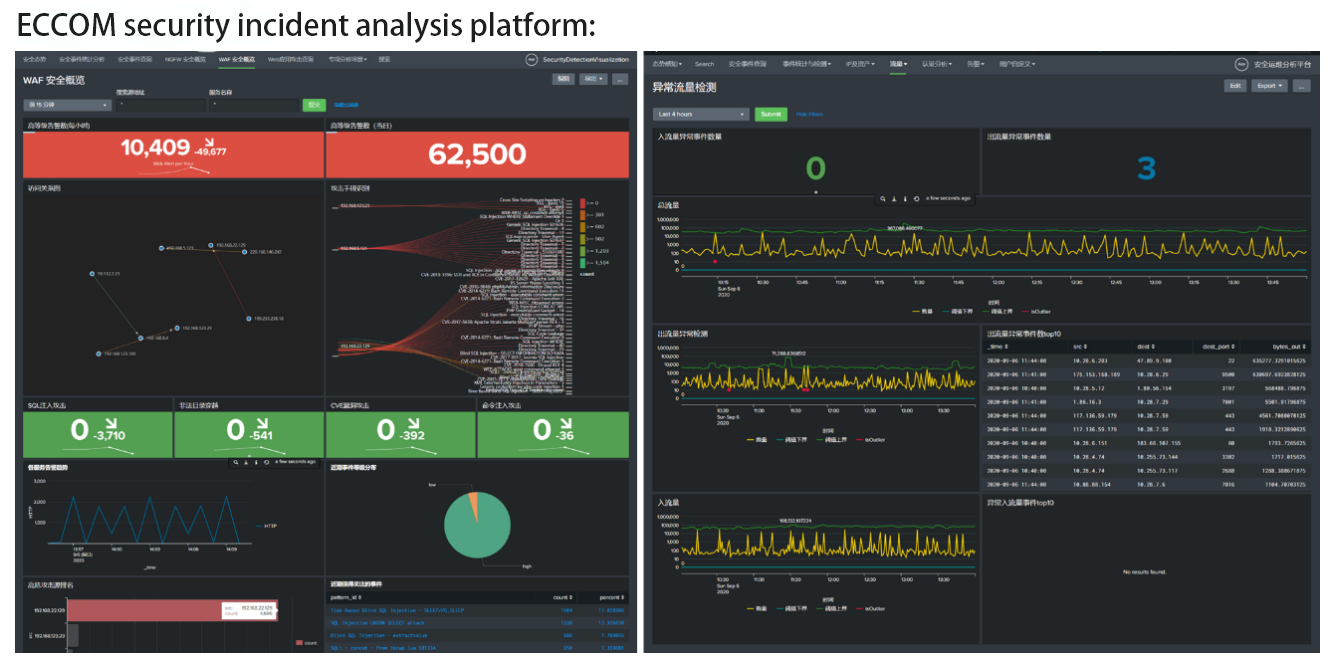
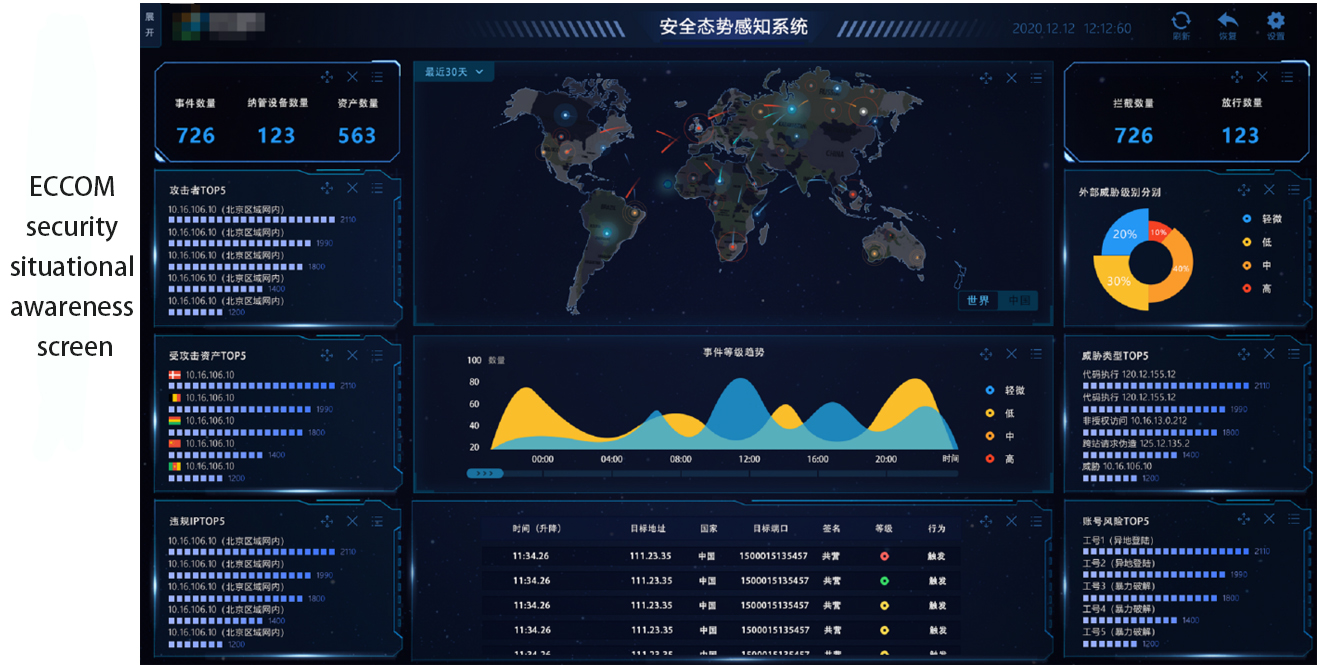
Establish a one-stop platform for collecting and visualizing security incidents, collect traffic data, visualize and analyze threats from different levels.
-

Attack traceability
Trace advanced threats through association analysis. All-directional and full-flow network traffic analysis and network backtracking forensics, to discover APT and other advanced threat incidents.
-

Emergency response
Adaptive response framework can be integrated with other security vendors to perform predefined automatic response operations
-

Operational capability improvement
Improve comprehensive management capability of its security operations team with external resources .
About us
-
About us
-
News
Service
-
Smart Service
-
Service Solutions
Data Center Full-Stack IT Architecture Integration
Infrastructure Operations Insight Analysis and Optimization
Business Migration To A Hybrid Cloud Environment
IT Infrastructure O&M Services For Chinese Enterprises Going Global
IT On-site Services For Multi-Branch Organizations
Enterprise IPv6 Application Transformation Consulting And Implementation
-
MSS
-
Smart Cloud Services
-
Security Services
-
海外服务en
Industry
-
Finance
Building Orchestratable Security Framework For Online Transactions
Low-Latency Trading Optimization Solution In Securities And Futures Markets
Network Construction Of Data Center Resource Pool
Backbone Network And Traffic Engineering
Full-stack IT For Urban Commercial Bank Data Centers
Building A BDR System For Data Center
-
Manufacture
-
Transportation
-
Government
-
Education and Medicine
-
Enterprise