-
Visualization
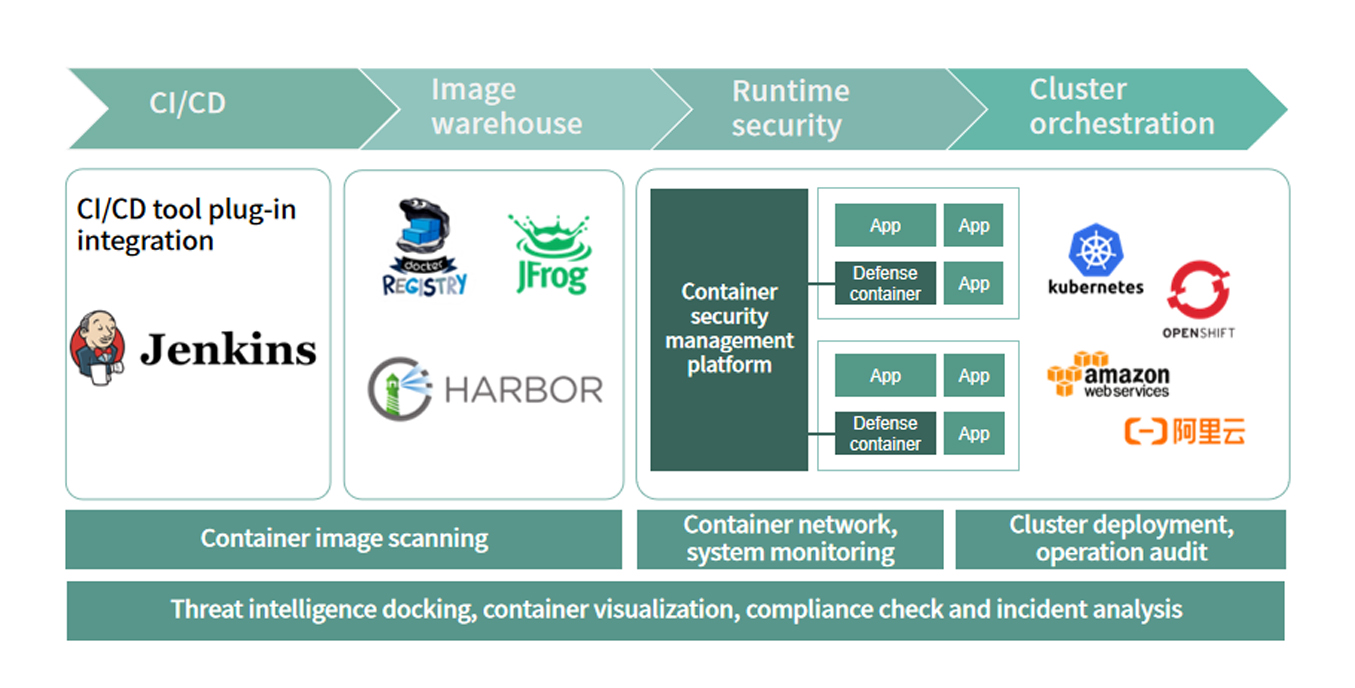
Eliminate security blind spots in the cloud native environment, discover anomaly inside containers rapidly, avoid known vulnerabilities and high-risk configurations.
-

Automation
Set up container compliance rules that meet enterprise requirements, and automatically check them regularly, so that the development team takes action as soon as possible, rapidly and easily .
-

Cloud native
Security measures must not affect the speed and agility of DevOps team, and therefore cloud native security solutions should be agile, flexible and lightweight.
-

Application protection
Introduce a security mechanism into the DevOps process and establish an application security baseline to improve security without hindering agility.
About us
-
About us
-
News
Service
-
Smart Service
-
Service Solutions
Data Center Full-Stack IT Architecture Integration
Infrastructure Operations Insight Analysis and Optimization
Business Migration To A Hybrid Cloud Environment
IT Infrastructure O&M Services For Chinese Enterprises Going Global
IT On-site Services For Multi-Branch Organizations
Enterprise IPv6 Application Transformation Consulting And Implementation
-
MSS
-
Smart Cloud Services
-
Security Services
-
海外服务en
Industry
-
Finance
Building Orchestratable Security Framework For Online Transactions
Low-Latency Trading Optimization Solution In Securities And Futures Markets
Network Construction Of Data Center Resource Pool
Backbone Network And Traffic Engineering
Full-stack IT For Urban Commercial Bank Data Centers
Building A BDR System For Data Center
-
Manufacture
-
Transportation
-
Government
-
Education and Medicine
-
Enterprise