Multidimensional security architecture
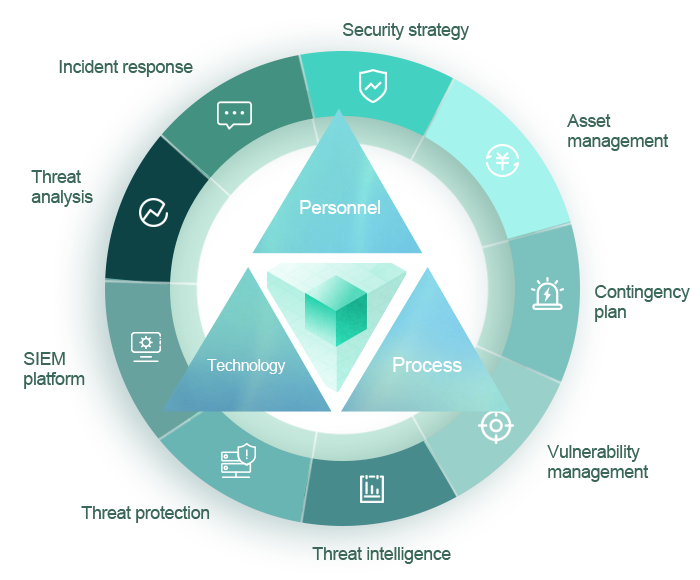
In ECCOM's multidimensional security architecture, the "terminal-network-data" deep protection system for a traditional data center has been extended to public cloud and private cloud platforms to establish a hybrid cloud security architecture in spatial dimension.
The generated massive logs, traffic and performance data are summarized in a security operations platform to conduct threat intelligence analysis, situational awareness and big data analysis, provide feedback for target objects, optimize policies and schedule resources at the time dimension.
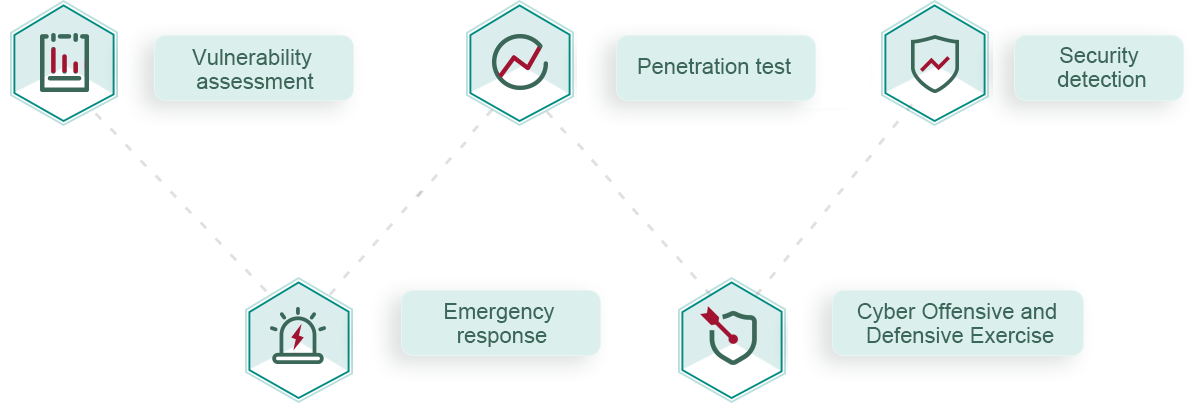
On the basis of security architecture without blind spots and perfect, effective security operations, effective security services are needed to transmit best practices by means of vulnerability assessment, security detection, emergency response, attack and defense drills, etc. With a 3-in-1 security business architecture, ECCOM helps more and more customers accelerate business innovation transformation and security system building.